Created: 11/03/2024 16:00 Last Updated: 22/11/2024 18:55
Our friend "Dee" was looking for a job in Tanta, but it seems she was hacked by one of the malicious websites, so can you examine her hard drive and find some evidence?
File Location: C:\Users\LetsDefend\Desktop\ChallengeFile\PDFURI.7z
WSL Username: letsdefend WSL Password: letsdefend
As soon as the machine is up, I extracted the 7zip file right away and Iook like I got an image to work with

Next I opened FTK Imager and add an image as the evidence
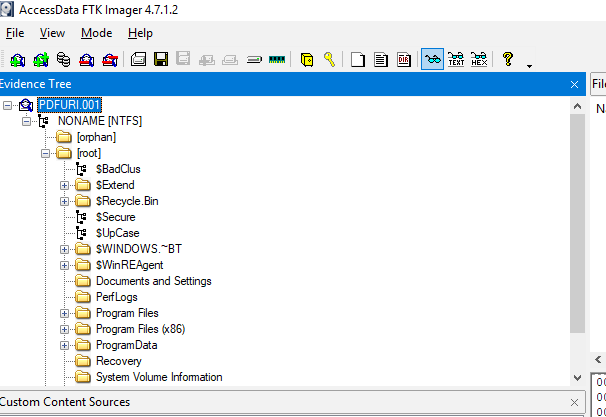
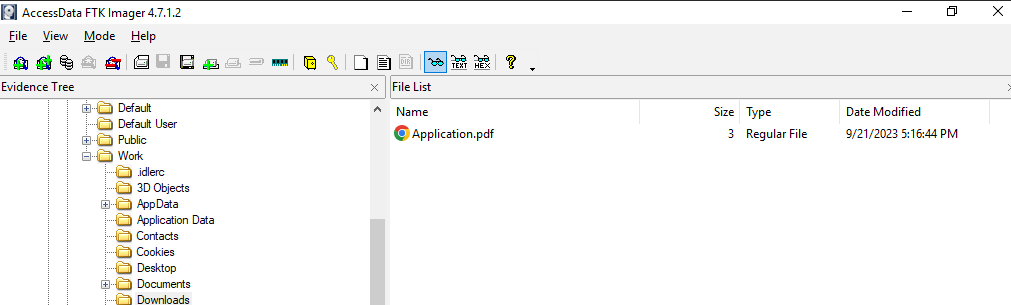
After scrolling for a while, I found that there is a user Work that is not the default user and within the Downloads folder, there is a pdf document file there
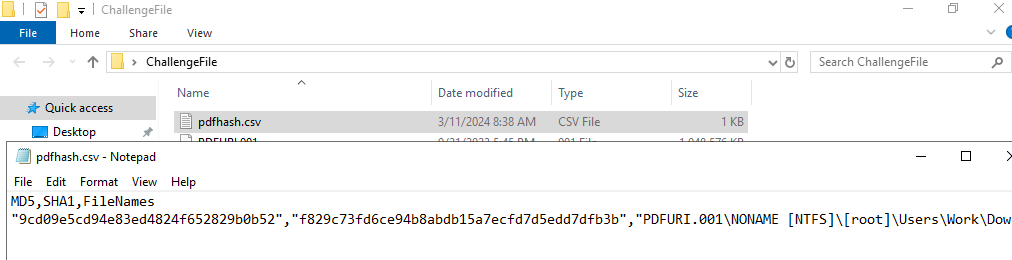
 I exported both hash and file then loaded the file to PDFStreamDumper
I exported both hash and file then loaded the file to PDFStreamDumper
 This is definitely a suspicious document or even malicious according to this challenge, It will run a powershell commands once it opened
This is definitely a suspicious document or even malicious according to this challenge, It will run a powershell commands once it opened
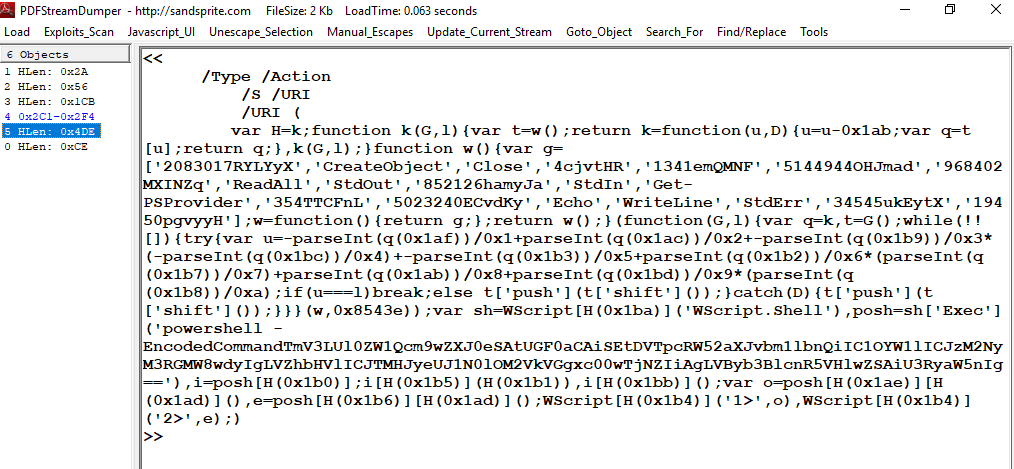 And After executing this command, a new registry entry with the name s3cr3tF1o0w and the specified value will be created under
And After executing this command, a new registry entry with the name s3cr3tF1o0w and the specified value will be created under HKEY_CURRENT_USER\Environment.
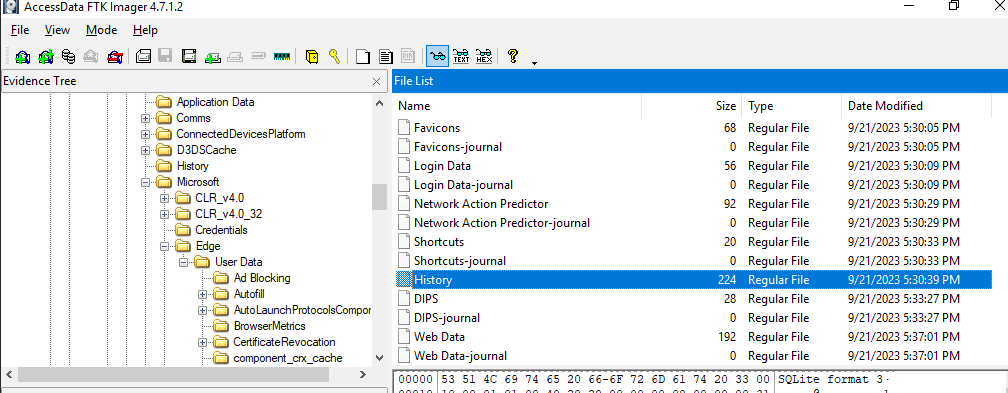
Next I went on \Users\Work\AppData\Local\Microsoft\Edge\User Data to find Microsoft Edge Browser Artifacts and export them as mush as needed
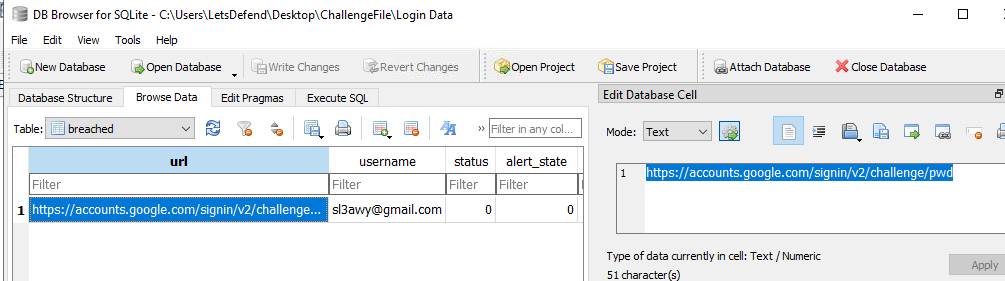
I opened them using DB Browser for SQLite
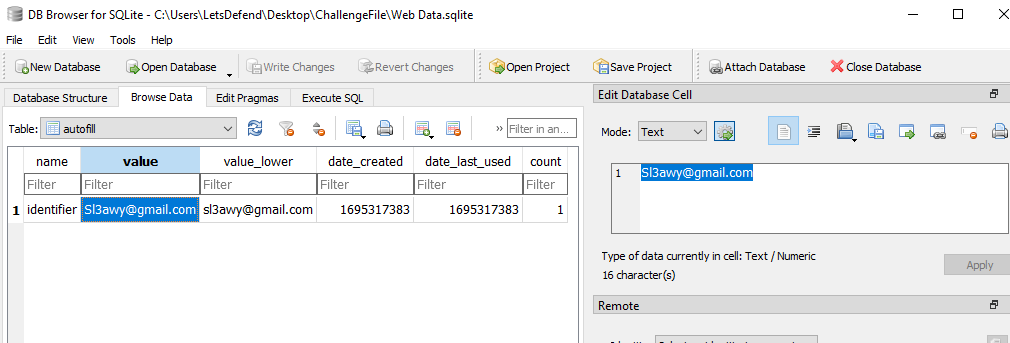
On Login Data, I've got an email on the user.
 and it also could be found on
and it also could be found on Web Data
 On
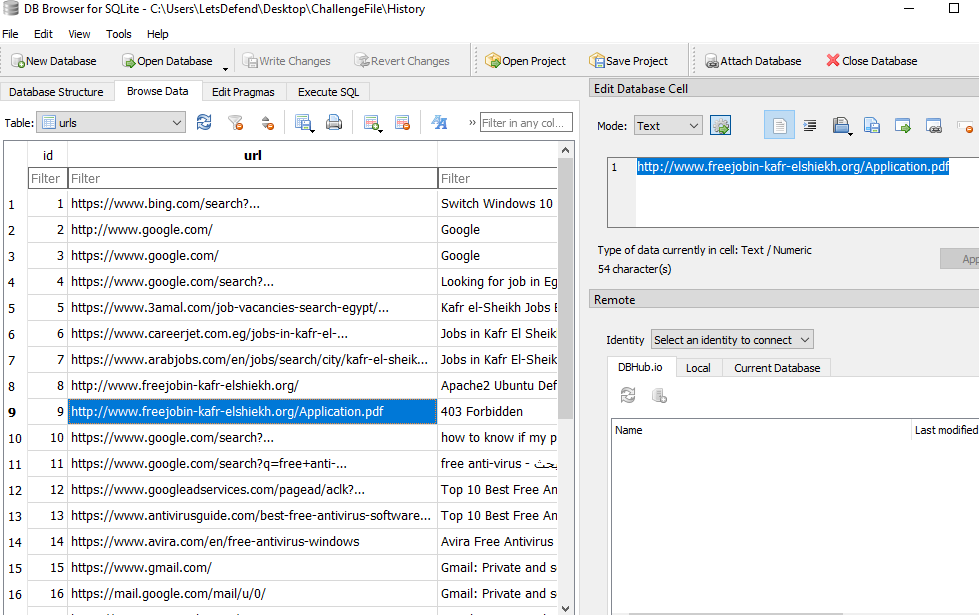
On History, I found the domain that the malicious document was hosted
And lastly to answer the final question, I went to find SAM registry hive then loaded to Registry Viewer
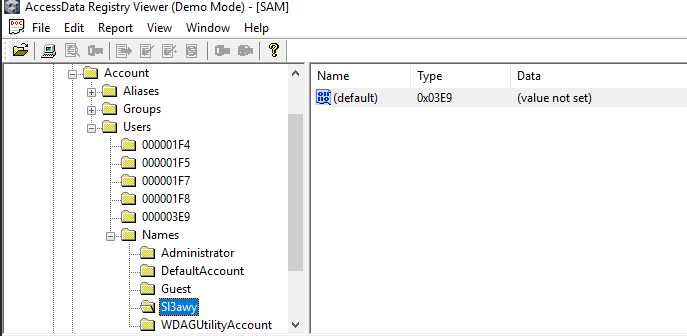
 Which I've found that there is no
Which I've found that there is no Work user anymore but instead Sl3awy were there so the user changed the username from Work to Sl3awy.
What is the MD5 hash of the malicious document?
9cd09e5cd94e83ed4824f652829b0b52
What is the domain from which the document was downloaded?
http://www.freejobin-kafr-elshiekh.org/
What is the email address of the victim?
Sl3awy@gmail.com
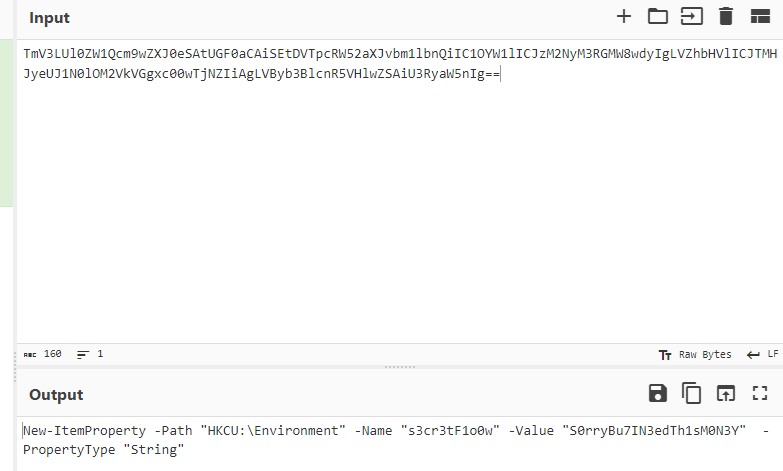
What is the command that is executed by the malicious document?
powershell -EncodedCommand TmV3LUl0ZW1Qcm9wZXJ0eSAtUGF0aCAiSEtDVTpcRW52aXJvbm1lbnQiIC1OYW1lICJzM2NyM3RGMW8wdyIgLVZhbHVlICJTMHJyeUJ1N0lOM2VkVGgxc00wTjNZIiAgLVByb3BlcnR5VHlwZSAiU3RyaW5nIg==
Seems the PC username changed to another one. Can you identify the new Username?
Sl3awy
On this challenge, We used FTK Imager to investigate Windows disk image to find the culprit of the incident which is malicious PDF file that will execute PowerShell command.